“We are encouraged by the collaborative activity we see underway,” said Shaun Reardon, Customer Success Director, Cyber Security in DNV. “But there needs to be much more industry collaboration to identify and counter threats before OT cyber security becomes a safety issue far larger and more acute than many boards and C-suites can imagine. OT cyber security risks are increasingly becoming business risks. There has never been a more important time for industry to come together to share knowledge, create best practice, and develop new standards in the fight against cybercrime.”
Playing ‘wait-and-see’ on cyber security
DNV research for our May 2022 report The Cyber Priority shows the importance of guiding directors and C-suites in how to promote a corporate culture that is cyber-aware and resilient.
Six in 10 C-suite level energy executives acknowledged that their organization are more vulnerable to cyber-attack than ever before. Significantly fewer (44%) expect to make urgent improvements in the next few years to prevent an attack. More than a third (35%) say their business would need to be impacted by a major incident before it would spend any more time or money on its defences.
“Some energy firms appear to be hoping for the best rather than proactively countering the cyber threat,” commented Reardon. “It reminds us of some 1970s’ oil and gas industry attitudes to physical safety practices. It took tragic incidents like Piper Alpha and Deepwater Horizon for the oil and gas sector to prioritize and institutionalize safety protocols, standards, and regulation.”
There is no reason why a similar transformation cannot be achieved in the field of OT cyber security, but without having to go through similar pain, he stressed: “As in the case of physical safety, collaboration and creating trust in processes, people, and technologies can be the keys to a step-change in both IT and OT cyber security across industrial sectors and their value chains.”
The Cyber Priority also indicates a need to maintain investment in cyber security for IT while ensuring that equivalent resources are available to protect against cyber-attacks on OT, Reardon added. A study of OT security professionals published by Applied Risk, a DNV company, in 2021 reveals that outdated and ageing control systems is the top obstacle to minimizing OT security-related risks.
Creating best practice and standards
Trust is vital. Companies are understandably reluctant to share OT cyber security experiences for fear of undermining confidence or highlighting vulnerabilities. They need a safe ‘space’ to report, collect, analyse and share lessons from cyber security incidents. Creating best practice and developing new standards in collaboration with industry peers can be one such safe space.
“I think it is fair to say that there is currently insufficient best practice available to guide operators, suppliers, manufacturers, and regulatory authorities in building effective cyber defences for OT,” said Reardon. “That said, we are already seeing industrial players come together to develop technical best practice.”
Outcomes of such cooperation include IEC 62443 standards for cyber security in OT in automation and control systems, and DNV Recommended Practice (RP) DNV-RP-G108 for applying IEC 62443 in energy and maritime industries. More than three-quarters of OT security professionals say their organizations use an OT-specific cyber security standard to manage their security programme, according to Applied Risk. The IEC62443 series is the most adopted standard for minimizing OT security risks among these organizations.
Recommended Practice DNV-RP-0575 also came from collaborating with industry. Describing 45 risk reducing measures – covering people, processes, and technology – this RP provides guidance to companies operating, managing, and securing existing power grid substations. For ships and mobile offshore units in operation, working with industry led to DNV-RP-0496, which gives guidance on cyber security resilience management.
Collaborating around the OT cyber security skills gap
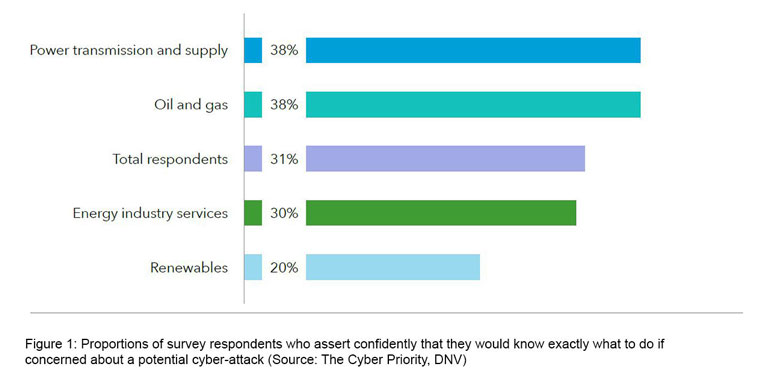
Greater collaboration, knowledge-sharing, and support across industries can also help to mitigate a large and growing cyber skills shortage. The skills gap reflects in less than a third of respondents to The Cyber Priority expressing confidence that they know exactly what to do if they became concerned about a potential cyber risk or unfolding attack (Figure 1). Speed of response is essential in such situations.
According to the ISC2 Cybersecurity Workforce Study, the cyber security workforce gap represents around 2.7 million professionals.3 Within energy, maritime and other sectors, the challenge is exacerbated by demand for specialist talent that understands OT as well as IT, and in the relevant industrial contexts. With the global shortage of such cyber professionals, companies need to collaborate to leverage shared experiences and knowledge, especially if they are small or medium-size operators.
“Some energy businesses don’t really have what could be described as IT teams, and certainly not teams focused on OT security. This is particularly true of the renewable energy companies we canvassed. Their senior professionals score lowest for incident-response awareness,” said Reardon.
Collaborating for smoother regulatory compliance
Voluntary collaboration can help to design and implement corporate strategies, processes, cultural attitudes, and training to ease compliance with existing regulations. It can also position companies to comply with less effort and cost to inevitable new and updated regulations mandating detection, identification, and reporting of actual or suspected cyber incidents.
Reardon noted: “With the safety and economic stakes so high, governments will become ever-more proactive and reactive with cyber regulations and laws to protect health, safety, the environment, and strategic infrastructure and assets. We are seeing this already – for example, after the Colonial Pipeline incident.” Following that cyber-attack, the US Federal Government issued a Security Directive in May 2021 ordering pipeline operators to check and report on the cyber security of their pipeline systems within a month.4
In the same month, US President Joe Biden issued an executive order which, among other things, triggered the setting up in 2022 of a Cyber Safety Review Board (CSRB). Government and industry leaders collaborate in the CSRB to review and assess significant cyber security events to better protect the US’s networks and infrastructure.5 The CSRB neither regulates nor enforces but identifies and shares lessons learned to promote national cyber security. Its first report included 19 actionable recommendations for government and industry to address the continued risk posed by vulnerabilities discovered in late 2021 in the widely reported Log4Shell vulnerability for the popular Java programming language. Log4Shell exemplifies risk originating in a supply chain. It was discovered in 2021 in a tool used in cloud servers and enterprise software globally, and in both IT and OT.
US vessels and facilities regulated under the country’s 2002 Maritime Transportation Security Act (MTSA) must report cyber security breaches or suspicious cyber activity to the US Coast Guard National Response Center. For cyber incidents that do not also involve physical or pollution effects, reporting parties can also report these to the National Cybersecurity and Communications Integration Center, which may be able to provide technical assistance. Guidance on such reporting has been in place since 2016, though it is unclear what the response has been.
On a global governance stage, the International Maritime Organization (IMO) provides demands and guidelines on cyber security for shipping. IMO’s cyber risk management resolution, effective 1 January 2021, requests shipowners, operators, and managers to ensure that every vessel’s Safety Management System includes Cyber Risk Management.
Developments in Europe signal more future cyber security compliance challenges for energy industries trading across borders and working within complex supply chains. A planned EU Action Plan on the digitalization of the energy sector is in preparation.6 It could include a focus on ‘enhancing the cyber security of the energy sector facing real-time requirements, cascading effects and the mix of legacy technologies with smart/state-of-the-art technology’, according to a roadmap for the plan. The Action Plan will align with the EU’s general framework for cyber security, known as the NIS Directive, which is currently being updated. There is also a planned European Network Code on Cybersecurity of cross-border electricity flows. The Action Plan will assess the need for additional measures for other aspects of energy industry cyber security if needed.
Industry collaborations on cyber security
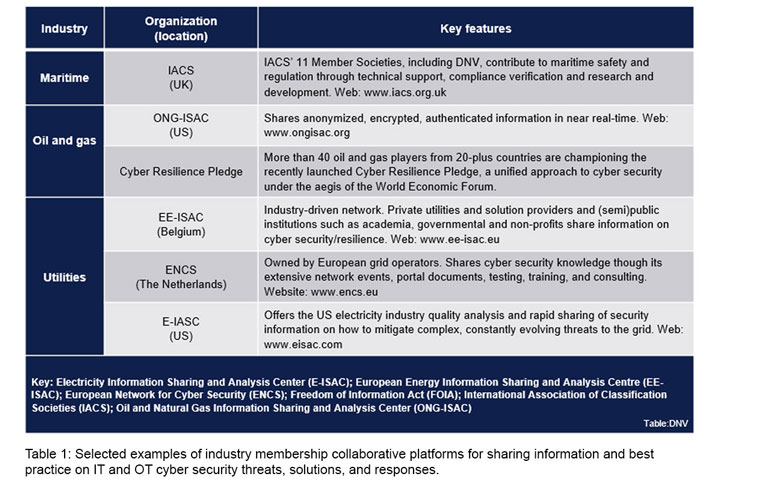
Industry collaborations are operating, emerging, and evolving (see Table 1) amid rising and shifting regulation and the need to avoid incidents that could jeopardize revenues and licences to operate.
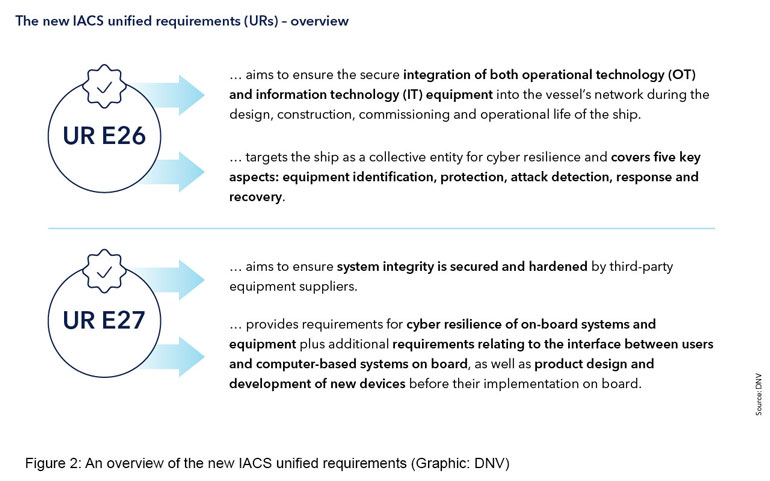
The International Association of Classification Societies (IACS) Unified Requirements (URs) oblige shipyards, as system integrators and system vendors, to build cyber security barriers into all newbuilding vessels and systems from 1 Jan 2024 (Figure 2).7 The URs apply to IT and OT systems and internal and external communication systems required by class rules and statutory regulations. The URs are minimum goal-based requirements for cyber resilience of new ships and cyber security of onboard systems and equipment. They emerged from extensive collaboration in a Joint Working Group on Cyber Systems set up by IACS.
IACS URs and DNV’s own class rules use IEC 62443 standards addressing OT and IT cyber security holistically and covering technical and process-related aspects. Drawing on discussions with the industry, DNV developed its own Cyber secure class notation addressing cyber security of a vessel’s main functions and the owner’s operational needs.
DNV is ready to apply IACS-compliant Cyber secure rules to newbuilds.8 More than 100 vessels are contracted so far for voluntary approval with DNV, as well as a larger range of automation and navigation system suppliers who are type-approving their systems.
Among collaborations watching and responding to EU regulatory developments is the European Energy Information Sharing and Analysis Centre (EE-ISAC). It could eventually integrate with a threat intelligence platform that enables real-time situational awareness. The idea is that considering fault and attack scenarios together would allow threat awareness to be transferred into operational contexts to prioritize decisions and responses.
EE-ISAC and European Network for Cyber Security (ENCS), owned by power grid operators are strengthening cooperation in threat intelligence across Europe. They will share information on vulnerabilities and threats against utilities and people across Europe. The intelligence will be used to reinforce resilience of the European grid system from cyber-attacks.
DNV leads and participates in collaboration
DNV recommends companies to consider four important issues when addressing cyber security: budget for cyber security; determine your vulnerabilities; maintain focus on your supply chain; and invest in people.
“These are sound principles, but we also call on industry to go further in taking collective action as industrial cyber security risks increasingly become business risks,” urged Reardon. “Industry collaboration providing insight, knowledge, know-how, mentoring and inspiration to assist companies on their OT cyber security journeys can bring benefits to businesses, industries, customers and society.”
However uncomfortable companies find it, it is important there is a shared and trusted space for them to share experiences and lessons, he concluded: “We have already seen this evolution in the oil and gas sector around safety, and we need to see the same happen in OT cyber security.”
Read more about DNV cyber security services
Reference:
1 'The Cyber Priority', DNV, 2022
2 'X-Force Threat Intelligence Index 2022', IBM, 2022
3 'A resilient cybersecurity profession charts the path forward', (ISC)2 Cybersecurity Workforce Study, 2021 [online] www.isc2.org
4 US pipeline operators face compliance with new cyber security directive after colonial pipeline attack
5 'Executive Order on Improving the Nation’s Cybersecurity', The White House, press release 12 May 2021
6 'Roadmap: Action plan on the digitalisation of the energy sector', European Commission, Ref. Ares(2021)4720847 - 22/07/2021
7 'IACS adopts new requirements on cyber safety', IACS, press release, 21 April 2022 [online] iacs.org.uk
8 Yards and vendors must act promptly to comply with upcoming IACS cyber security requirements



